In today’s digital landscape, the importance of cybersecurity cannot be overstated. As cyber threats continue to evolve, understanding the tactics employed by adversaries is crucial. One such framework that has proven invaluable in this endeavor is the Cyber Kill Chain. This model outlines the stages of a cyber attack, providing a structured approach to understanding and defending against threats. Next, we will delve into the seven steps of the Cyber Kill Chain using a Lockheed Martin’s infography as reference. You will be able to find the complete infography here!
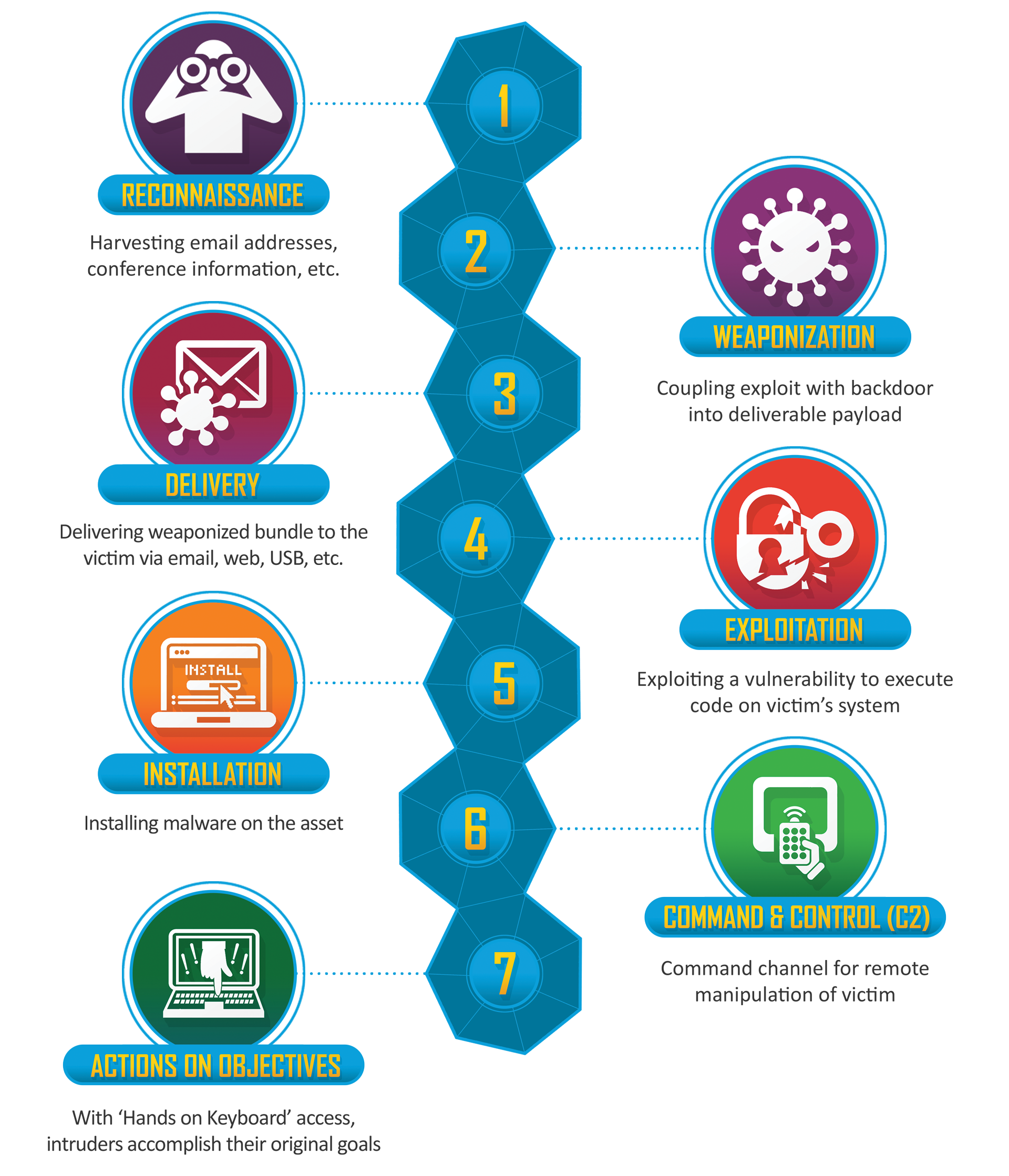 Cyber Kill Chain. Source: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Cyber Kill Chain. Source: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Stage 1: Reconnaissance
The first phase, Reconnaissance, involves the collection of information about the target. This step is akin to an attacker casing a physical location before planning a heist. Here, cyber adversaries gather data on the target’s infrastructure, personnel, and vulnerabilities. This may include open-source intelligence gathering, domain name system (DNS) enumeration, and social engineering techniques. Defenders can counteract this phase by monitoring public sources of information and implementing strong access controls.
Stage 2: Weaponization
In the Weaponization phase, the attacker creates a malicious payload, often in the form of malware, to exploit a vulnerability discovered during reconnaissance. This payload is crafted to evade detection. It is crucial for organizations to stay updated on security patches and utilize robust endpoint protection to mitigate the risks associated with weaponization. You can find a complete post about Malware here!
Stage 3: Delivery
The Delivery phase involves the transmission of the weaponized payload to the target environment. This can occur via various channels, including email, websites, or even physical media. Attackers may employ techniques like phishing emails or drive-by downloads. Implementing email filtering, web filtering, and awareness campaigns for employees about safe browsing habits are essential defenses against this phase.
 Malicious Emails. Source: Google
Malicious Emails. Source: Google
Stage 4: Exploitation
Once the weaponized payload reaches the target system, the Exploitation phase begins. The malware executes its code, taking advantage of the vulnerability it was designed to exploit. Timely application of security patches, regular vulnerability assessments, and network segmentation are key measures to thwart exploitation attempts.
 Arbitrary Code. Source: Google
Arbitrary Code. Source: Google
Stage 5: Installation
In the Installation phase, the attacker establishes a persistent presence within the compromised system. This may involve the installation of backdoors, rootkits, or other stealthy techniques. Employing strong authentication mechanisms, monitoring for anomalous activity, and conducting regular security audits can help detect and mitigate unauthorized installations.
Stage 6: Command and Control
With a foothold in the target environment, the attacker seeks to establish a communication channel back to their infrastructure. This phase, known as Command and Control, allows the attacker to remotely manage the compromised system and exfiltrate sensitive data. Employing network traffic monitoring, intrusion detection systems (IDS), and firewalls with advanced threat detection capabilities are crucial in detecting and preventing command and control activities.
 Remote Control. Source: Google
Remote Control. Source: Google
Stage 7: Actions on Objectives
The final phase, Actions on Objectives, is where the attacker achieves their ultimate goal. This could involve data theft, disruption of operations, or other malicious activities. Implementing robust data encryption, access controls, and advanced threat detection systems can significantly mitigate the risks associated with this phase.
Conclusion
Understanding the Cyber Kill Chain provides organizations with a powerful framework for comprehending the lifecycle of a cyber attack. By breaking down the attack process into distinct phases, organizations can implement targeted security measures at each stage. This proactive approach is essential, helping organizations stay one step ahead of attackers and safeguard their valuable assets.